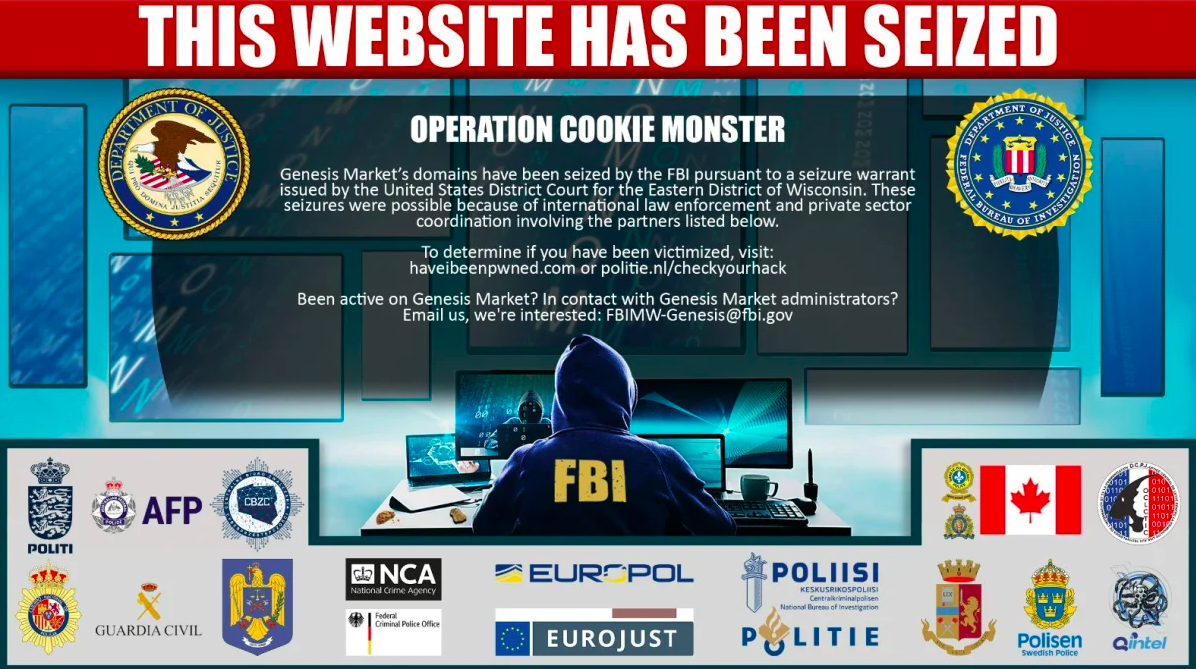
Genesis Market has been taken down in an operation involving judicial and law enforcement authorities in the United States, nine European Union countries, Australia, Canada and the United Kingdom. Genesis Market was a criminal marketplace accessible on the dark web and clear web that sold packages of account access credentials – including usernames and passwords for email, bank accounts, and social media. The credentials had been stolen from malware-infected computers around the world and were subsequently used by cybercriminals to commit cyber-enabled fraud. In a coordinated action supported by Eurojust and Europol, the infrastructure and operations of Genesis Market were dismantled and law enforcement in 13 countries conducted more than 100 arrests and more than 200 searches of Genesis Market customers who had purchased stolen access credentials.
Since its inception in 2018, Genesis Market was one of the largest facilitators of cybercrime. Its main criminal commodity was digital identities. The illicit website offered for sale what the market owners referred to as ‘bots.’ These bots were basically packages of stolen credentials harvested from infected computers around the world. Genesis Market’s administrators obtained this victim data through malware deployments and account takeover attacks. At the time of the takedown, Genesis Market was advertising for sale account credentials stolen from approximately 460,000 computer devices located in almost every country in the world. Customers of Genesis Market could use these credentials to gain illegal access to victims’ computer systems, which would then allow them to commit further cybercrimes.
Genesis Market customers were located all over the world and actively purchasing stolen packages of victim data until this takedown. The U.S. FBI has worked with its law enforcement partners to identify prolific users of Genesis Market who have purchased and used stolen access credentials to commit fraud and other cybercrimes. The U.S. Department of Justice also worked with its judicial counterparts through Eurojust to ensure coordinated action. This effort resulted in hundreds of leads being sent by the FBI to law enforcement partners in Australia, Canada, Denmark, France, Germany, Italy, the Netherlands, Poland, Spain, Sweden and the United Kingdom.
As part of the coordinated effort referred to by law enforcement agencies as Operation Cookie Monster, on 4-5 April, more than 100 suspects were arrested and 200 property searches were conducted in 13 countries. In addition, the infrastructure and main domains of the criminal website were seized and taken down.
Eurojust actively facilitated the cross-border judicial cooperation between the national authorities involved. Eurojust hosted a coordination meeting in March 2023 to prepare for this week’s operation and hosted a command centre on 4 April to resolve any legal issues arising during the parallel operations in 13 countries.
Europol’s European Cybercrime Centre (EC3) has been supporting this investigation since 2019 by coordinating the international activities with the help of the Joint Cybercrime Action Taskforce (J-CAT), hosted at Europol. EC3’s support included data analysis, organising operational meetings and facilitating the exchange of information. A command post was also set up at Europol’s headquarters in The Hague, the Netherlands to ensure the smooth running of the action day across the world.
The Dutch authorities have developed a portal to help potential victims check whether their digital identity has been stolen. Visit politie.nl/checkyourhack and fill in your email address to check whether your credentials were available on Genesis Market. In addition, victim credentials obtained over the course of the investigation have been provided to HaveIBeenPwned.com, and potential victims may also check the HaveIBeenPwned.com website to see if their credentials were compromised so they know whether to change or modify passwords and other authentication credentials.
If your digital identity has been stolen, here are the steps you should take:
- Run your antivirus programme. In most cases, your antivirus will catch the malware and remove it. Only then should you change all your passwords – not before, unless you want the cybercriminals to get their hands on them.
- Notify relevant stakeholders. Your bank, insurance company and any other important third party should be made aware of your identify theft.
The following countries took part in this investigation:
- Australia
- Canada
- Denmark
- Estonia
- Finland
- France
- Germany
- Italy
- Poland
- Spain
- Sweden
- The Netherlands
- United Kingdom
- United States
Source: Eurojust