Andy Scherpenberg
We know it is coming. And yet, we aren’t ready. Of course we saw a decline in the use of banking malware. Why would a criminal spend time, effort and money to develop a software that defrauds a banking customer if you can just ask their credentials over the phone? Indeed: low cost, highly efficient social engineering took the fraud world by storm when it proved utterly easy to scare people into revealing their login, password and authentication codes.
Soon after, vishing was all over the news. Panicked by the onset and fearing increasing losses and possibly even more painful reputational damage, banks jumped the bandwagon. Either with self-developed or supplier-provided tools, they started an unfair fight against the incoming waves of fraud attempts. Even the government got involved.
Finally, the combination of interbanking cooperation through sector federations, the fraud-detection software at banks, and educating the public has significantly reduced the vishing volumes. Still, certain banks where the fraud detection system is overly simplistic and/or where they have a more vulnerable customer base keep being affected, but the bulk of the vishing is gone.
Bad guys have business plans too!
But then again, fraudsters need to earn a living too. They have business plans, reports and KPI’s. And not reaching those could have far more dire consequences than being fired (in their situation, maybe literally). So they change their playing field. Sticker fraud, CEO fraud, phone banking fraud, there is a broad portfolio. And they try. If it doesn’t work, they change. To a working method where the results outperform the efforts. It’s all about a strong ROI. Which brings us back where we started. Malware. Not the unrefined, relentlessly spreading variant of years past with an easily discernible signature. The older forms relied on infecting non-updated Windows PC which don’t run a virus scanner (unfortunately, there are still many). No, the new forms are refined. Sophisticated. They are polymorph and adapt themselves as they spread. They are targeted, deliberately limiting their infections to delay discovery by vigilant anti-virus providers. They operate invisibly. A man-in-the-browser malware yields additional difficulties for customers and banks. For one: the customer has no view on what is actually happening. And the bank sees a login from a properly authenticated customer on a known end-point. Yet in the background, the fraudster decides how much money goes to which account.
Invisibility cloak
And we’re not even talking about the malware which is already roaming the banks worldwide which could enable criminals to initiate transactions from within. You haven’t seen it yet? Then let this sink in: the Red October Cyber-espionage malware was built in 2008 and had been operating for 5 years before it was found. Imagine what they are building today.
Stay calm … and panic!
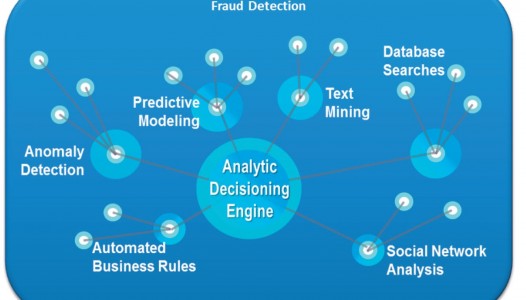
So how do we cope? How should we arm ourselves against a new onslaught of fraud attempts? The solution does not present itself at the same level as the problem. It needs an overarching approach. Awareness, communication, prevention through asset identification, encryption and possibly even isolation, those are all elements that will play an important role in any serious framework. And where will we put our faith for the detection? It should not come as a surprise that abandoning the old methods would be a dire mistake. We need to make them relive in a contemporary flavour. Trend Micro’s global virus and malware repository for instance, where once a malicious code is identified, its signature is automatically pushed to all subscribers. Or CheckPoint’s sandbox approach, where an email or downloaded macro-enabled document’s behaviour is checked before releasing it from quarantine. But that will not suffice. As experts agree, network, endpoint and user behavior analytics will unlock the next level. By profiling them, abnormal behavior can be detected at those levels where malware manifests itself.
If you find the needle, the haystack is already gone…
Efficient and effective analytics are key protecting our assets, be it knowledge or funds. It’s equivalent to catching the drop from the waterfall before it floats out of the lake. Luckily, dropping prices for commodity hardware, CPU power and memory make this a reality, already today. Now we only need to act, or blame ourselves afterwards when we wish we did.
Learn more: Leveraging Analytics to Combat Digital Fraud in Financial Organizations : http://go.sas.com/5rfj44
The author, Andy Scherpenberg, is a Solution Specialist Fraud & Security at SAS.